Secure Database Access
Protect Your Database Management Environment with Advanced Security

Multi-layered encryption secures all communications
Require multiple methods to prevent breaches
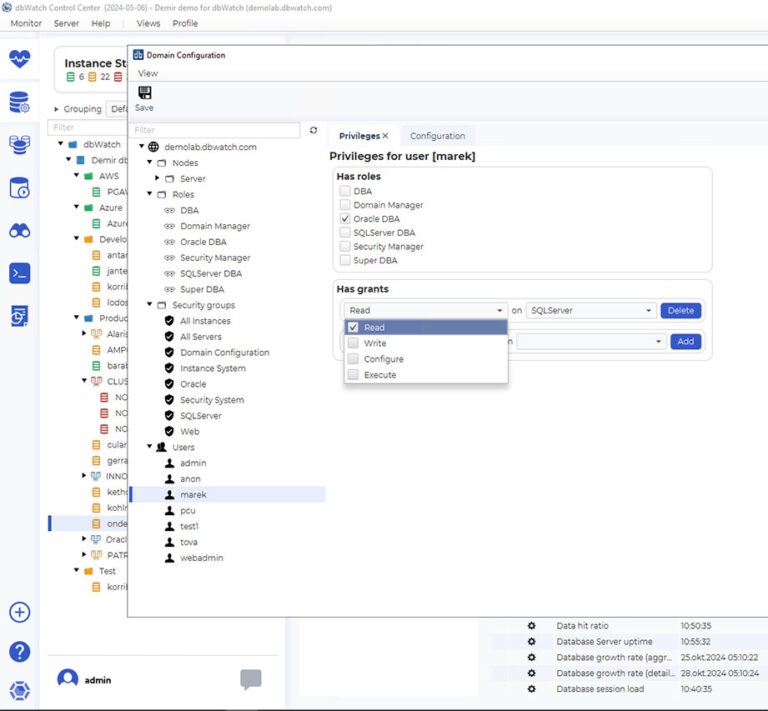
Grant safe, limited access to data for developers and DBAs
Track and audit all user activity and tool usage securely
In simpler English: with multiple encryption layers you will stay safe even if there are security problems for the encryption technology in the future.

Grant secure, controlled access to developers and DBAs without compromising production environments.
Start a free trial to explore multi-layered encryption, customizable permissions, and advanced access controls tailored to your needs.
Choose your subscriptions and know what's happening in dbWatch!
You can unsubscribe at any time. Privacy policy
You have successfully joined our subscriber list.
+47 22 33 14 20 (Oslo)
dbWatch AS
Nedre Slottsgate 4M
0153 Oslo, Norway