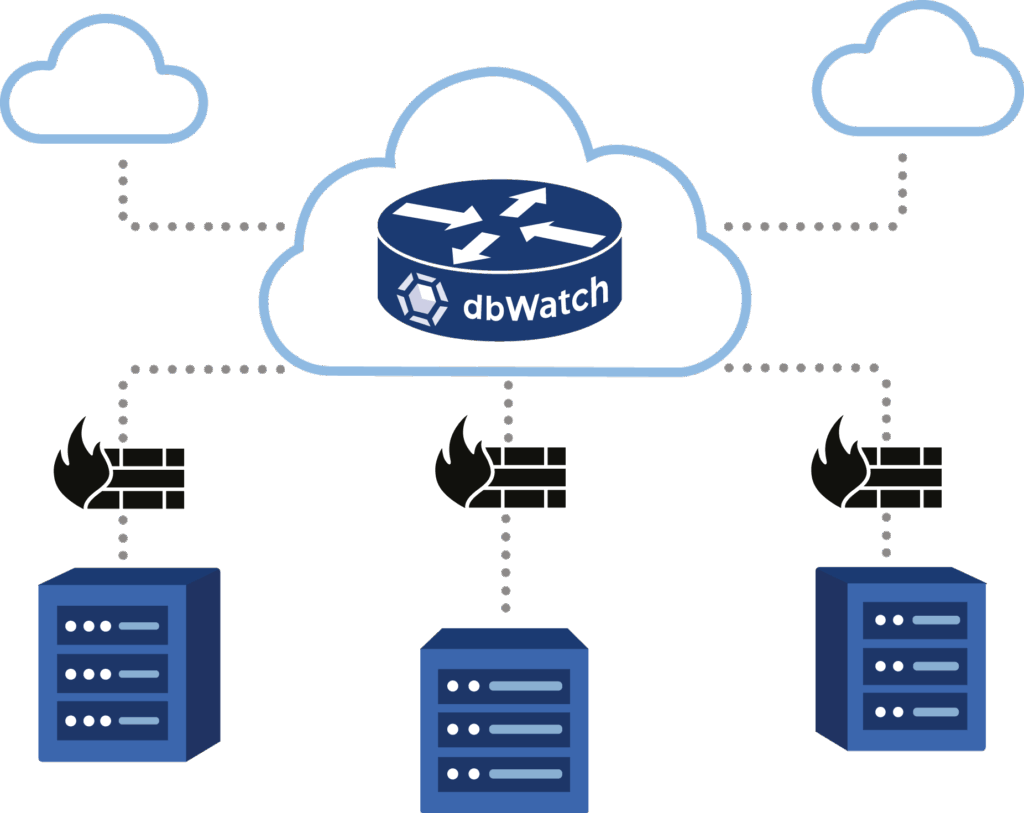
Secure Network Connectivity
Enable secure and safe communication between networks
- Connect databases across multiple security zones or geographic locations without inbound firewall openings.
- Maintain strict data isolation through encrypted “bubbles,” ensuring sensitive data remains hidden, even in the event of a breach.
- Multiple encryption layers provide protection for all your communication channels.